
SGBOX NEXT GEN SIEM & SOAR
ALL-IN-ONE
Scopri come SGBox può aiutarti a proteggere la tua infrastruttura IT e i dati sensibili.

con il Cloud di SGBox in modalità SaaS.











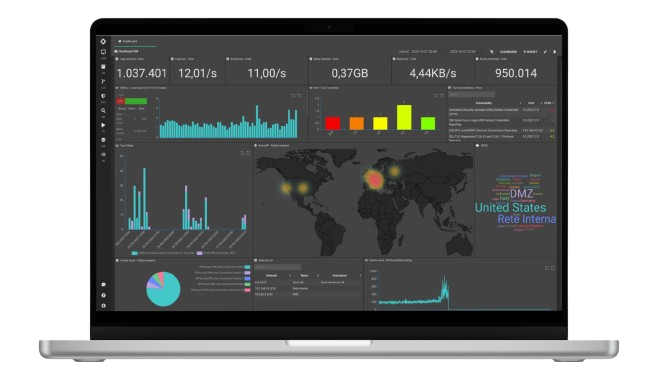
La Piattaforma SIEM e SOAR per gestire la Sicurezza ICT
SGBox è una piattaforma SIEM & SOAR all-in-one, modulare e scalabile, che permette di proteggere la tua infrastruttura IT contrastando ogni tipo di minaccia informatica in modo efficace.
SGBox ha come obiettivo la raccolta centralizzata dei log, l’analisi, la correlazione e il monitoraggio di un elevato numero di dati provenienti da ogni tipo di sorgente, in conformità con le normative sulla privacy.
Network Visibility
Un unico punto di vista per monitorare la sicurezza.
Security Analytics
Individua e accerta le minacce utilizzando analisi avanzate.
Integrity Monitoring
Tieni traccia dei cambiamenti non autorizzati sui dati.
Auditing
Audit trail per utenti, processi e policy.
Costo fisso indipendentemente dal volume
La prima piattaforma SIEM & SOAR con un prezzo predicibile e un modello di licenza trasparente.
Il costo della licenza è basato sul numero totale dei device che inviano log, non sul numero di eventi per secondo (EPS).
Funzionalità della piattaforma SGBox
SGBox SIEM & SOAR al centro della Governance
SGBox è uno strumento facile da usare, efficace e affidabile che presenta caratteristiche uniche.
Alla base di SGBox c’è il concetto di modularità. Tutti i moduli della piattaforma funzionano in sinergia per fornire un’interfaccia semplice e intuitiva per monitorare lo stato di sicurezza della tua rete, ed individuare prontamente le potenziali minacce.

Prodotti di Sicurezza Informatica
SIEM
Raccolta centralizzata, correlazione e analisi dei dati provenienti da diverse fonti.
Incident Management
Gestione degli incidenti e delle anomalie riscontrate dagli altri moduli della piattaforma.
SOAR
Automatizza i processi di sicurezza consentendo una risposta rapida ed efficace agli attacchi.
Log Management
Raccolta di qualsiasi tipologia di log in conformità con le normative sulla privacy.
Cloud SIEM
Sfrutta le potenzialità del SIEM con la flessibilità del Cloud, all'interno del quale vengono conservati i dati.
User Behavior Analytics
Analisi e monitoraggio del comportamento degli utenti e intervento in caso di anomalie.
Advanced Event Search
Informazioni dettagliate sui problemi riscontrati sulla rete.
Threat Intelligence Feed
Analisi dei feed di intelligence per prevenire le minacce prima che si verifichino.
Network Vulnerability Scanner
Identifica le vulnerabilità e le configurazioni errate nell'infrastruttura IT.
File Integrity
Monitoraggio dell'integrità dei file e di eventuali anomalie.
Active Directory Auditor
Monitoraggio dello stato delle Active Directory.
Event Correlation
Crea regole di correlazione per abbattere i tempi di reazione ad una minaccia.
UI/UX Design
Build the product you need on time with an experienced team that uses a clear and effective design process.
Dedicated Team
Build the product you need on time with an experienced team that uses a clear and effective design process.
Rete di Partner nel mondo
SGBox fornisce tutte le funzionalità della piattaforma grazie ad una solida e dinamica attività con le aziende partner, attraverso un canale 100% indiretto.
L’obiettivo delle Partnership è rafforzare l’expertise nelle differenti aree di competenza, per garantire elevati standard qualitativi nel supporto e assistenza al cliente.
Il nostro programma di Partnership è costruito su 3 livelli, ed offre numerosi vantaggi.
CYBERTRUST 365: MANAGED SECURITY SERVICE PROVIDER
CyberTrust 365 è la Business Unit di SGBox dedicata all’offerta di servizi di sicurezza gestiti, che vanno dal semplice supporto di 1° livello per la manutenzione evolutiva sino al servizio di Managed SIEM e SOC 24/7, per ottenere il massimo della protezione dagli attacchi informatici.
Leggi le nostre ultime novità
// Contattaci e ti aiuteremo a trovare il prodotto IT più adatto alle tue esigenze








